New Regulations on Protection of Personal Payment Information: Clarifying the Scope of Security Protection
[ad_1]
According to the China Payment and Clearing Association, in order to adapt to the latest requirements of national laws and regulations and better serve the development of the industry, the China Payment and Clearing Association recently revised the group standard “Guidelines for Personal Information Protection Technology” issued in 2016 and renamed it “Personal Information Protection Technology Guidelines”. Payment Information Protection Guidelines (hereinafter referred to as the “Guidelines”). The “Guidelines” are used to guide the services and activities of the member unit information systems of the Payment and Clearing Association of China to process personal payment information.
According to reports, the “Guidelines” standardize the definition and scope of personal payment information, and put forward the basic principles of personal payment information protection, security framework, security protection scope, business entities and main obligations, organizational construction, personnel management, terminal and business system security etc., and put forward typical protection requirements for different business scenarios.
Clarify the classification and security framework of personal payment information
Specifically, the “Guidelines” clarifies the classification of personal payment information – refers to any information involved in an individual’s participation in payment activities, that can be known and processed, that is related to the individual, and can identify the individual alone or in combination with other information, including Account information, authentication information, payment transaction information, personal identity information, in addition to specific personal payment information subjects’ consumption intentions, payment habits and other derived information, as well as other personal information acquired, processed and stored in the process of providing payment services information.
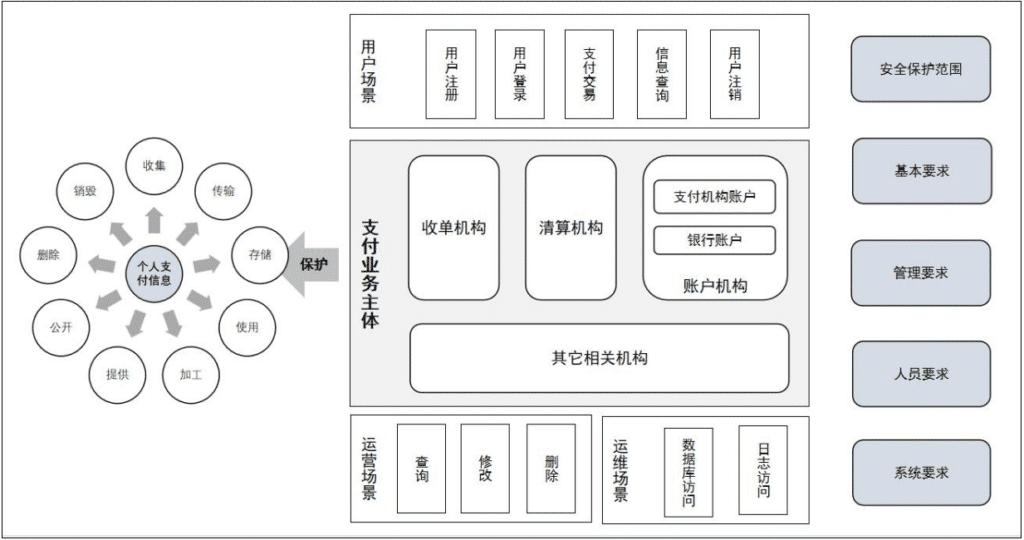
In addition, the “Guidelines” put forward three elements in the personal payment information security framework, which are payment business entities, business scenarios and payment technologies. Payment entities should carry out information protection work according to the main categories of payment information, identify the main responsibilities of various payment business entities, determine the scope of their own security protection, and establish security protection in accordance with different dimensions such as basic requirements, management requirements, personnel requirements, and system requirements. Personal payment information protection capabilities; in business scenarios, personal payment information protection needs to achieve full coverage of the scenarios. According to different payment service participation roles, data protection in user scenarios, business operation scenarios, and system operation and maintenance scenarios needs to be considered; payment technology should be based on Different payment technologies set specific requirements for the protection of personal payment information, including different technical models such as online payment, mobile payment, and bank card acquiring.
Personal payment information security framework. Source: “Guidelines for the Protection of Personal Payment Information”
For payment business entities, the “Guidelines” stated that the protection of personal payment information needs to cover the following three categories: system components, personnel and processes that directly collect, store, process and transmit personal payment information; System components of payment information, but they can be connected to system components that store, process or transmit personal payment information, and there is no effective control and audit of system components, personnel and processes for their access behavior after connection; it may affect the processing of personal payment information Environmentally safe system components, people and processes.
Clarify the management requirements of practitioners and their personnel
The “Guidelines” put forward management requirements for different payment business topics for the organizational structure of the practitioners, the person in charge of personal payment information protection, management systems and job settings.
In terms of organizational structure, practitioners should establish an organizational structure for personal payment information protection and provide necessary resources to ensure their independent performance of duties; in terms of personal payment information protection, the person in charge should have relevant management work experience and personal information protection professional Knowledgeable personnel are responsible for participating in important decisions related to personal information processing activities; in terms of management systems, personal payment information protection should be incorporated into the company’s overall risk management and internal control processes, and a decision-making mechanism suitable for institutional conditions should be established to make effective decisions Process; in terms of post setting, each payment business entity should reasonably set up personnel posts according to its own business characteristics, and clarify the responsibilities and overall requirements for personal payment information protection of internal departments at all levels of the organization and relevant posts.
In addition, the “Guidelines” put forward clear requirements on personnel recruitment, training, job transfer or resignation of practitioners, and management of violators. Payment business practitioners need to conduct necessary background checks when recruiting personnel to ensure that employees have not participated in harmful activities. Cardholders pay information security or other information leakage incidents, and sign a confidentiality agreement and information security responsibility commitment; in terms of employee training, employees should be arranged to participate in payment information security training in a timely manner before they start their jobs, and payment information security related training should be conducted at least once a year. Training or publicity to improve employees’ awareness and skills of payment information security protection; when employees transfer or leave, all access rights to payment information of resigned employees should be immediately changed, frozen or deleted, and relevant ID cards, keys and other items should be retrieved immediately As well as the software and hardware equipment provided by the organization, they should go through strict transfer procedures and require them to fulfill their confidentiality obligations; in terms of management of violators, employees who violate the payment information security management regulations and cause C2 and C3 payment information leakage incidents should be investigated. For punishment, if the circumstances are serious, the personal information of the violating employee should be reported to the relevant supervisory department and the reason for reporting should be indicated. If the violation is suspected of a crime, it should be reported to the public security organ in a timely manner.
The “Guidelines” also require that payment business entities should design personal payment information protection strategies according to different scenarios, establish basic requirements for personal payment information protection, and implement them correctly and effectively in the payment business system. For example, the information protection of the user payment scenario includes at least user registration, user information change, user login, payment, transaction query, user logout, etc.; the information protection of the operation scenario mainly includes operations such as information query, modification, and deletion by operators; the operation and maintenance scenario Information protection mainly focuses on the protection of information such as databases and logs. (Intern Wang Dinglun also contributed to this article)
[ad_2]
Source link